Needed to install and chain a SSL cert on a Citrix Netsclaler. Here is how to do it, Digicert style.
How to disable SIP ALG on a Forinet firewall
We had an office that was using Vontage for VOIP services. When we rolled in a new FortiWifi 90D in, they started to have issues. Two out of three times, the inbound call had no audio but the third time, it would work. To resolve this issue, we did the following.
Enter the following commands from CLI:
config system settings
set sip-helper disable
set sip-nat-trace disable
You will then want to reboot the device.
One the box has rebooted, open the CLI and enter the following commands – do not enter the text after //:
config system session-helper
show //locate the SIP entry, usually 12, but can vary.
delete 12 //or the number that you identified from the previous command.
Disable RTP processing as follows:
config voip profile
edit default
config sip
set rtp disable
Time Warner Business Class Internet (Cable) Install
I had Ordered Time Warner Business Class Internet for a satellite office that needs to be up and running as quick as possible. The order process was quick and painless. A bit on the expensive side ($500+ for Business Class 100M/10M) but we needed it very quickly and the building in question has very limited Internet providers. Within 45 minutes, I had the account setup and they scheduled the install for two days later. I was told it would be between 8AM – 12PM. The install date comes goes and no one calls or even shows up. The next day I get an email saying that I now have a new appointment for the next day between 1PM – 5PM. I call up the install scheduling group and ask what happened. She tells me that the installer was on site but no one was there. I tell her that we left two phone numbers for the installer to call and he called none of them. I also explain to her that there is an office manager onsite. She then tells me the installer “got there a bit late”. I ask how late and she goes “6:30PM”. I hope it gets better from here.
Dear Customer, you are responsible for installing power for our new FLASHWAVE 4100 that will be shared by all future customers in the building

Our IPVPN/ESIP provider is XO and they do appear on Tier 1 provider lists. A lot of times we have to “Type 2” over LEC’s to get service into some of our locations. Lately I have been running into situations where AT&T, Verizon, and Quest are the LEC/Last Mile and want us to pay for shared infrastructure. The latest one is for a location in Southern California where Verizon is out of capacity and needs to install a Fujitsu FlashWave 4100. The want us to install electrical and grounding for it at a cost of $1000. Once it is installed, they will run our circuit through it as well as being able to run other customers through it at a later day. Question is, why should we have to foot the bill for getting power to it? I get that they are out of capacity and we need the service but it just seems like there would be a better way to spread out or share the costs.
How to specify interface as source for ping on a Fortinet
From the CLI Console:
# execute ping-options view
Which will display the current interface. Per the example below, it has “Auto” as the Source Address.
Ping Options:
Repeat Count: 5
Data Size: 56
Timeout: 2
Interval: 1
TTL: 64
TOS: 0
DF bit: unset
Source Address: auto
Pattern:
Pattern Size in Bytes: 0
Validate Reply: no
Sending a ping out of the IP of an interface, where 192.168.76.1 is the interface bound address:
#execute ping-options source 192.168.76.1
exec ping 192.168.107.55
Supported Upgrade Paths to FortiOS 5.2.2
What is my upgrade path from this version to that….
What happens when you can’t reset a lost admin password on a Fortinet 100D?
I had a 100D that I had forgotten what I had set the admin password to. I followed this document that explains how to gain access and reset the admin password:
http://docs.fortinet.com/d/fortigate-restting-a-lost-admin-password
This did not work no matter how many times I tried it. There is a 14 second window in which you need to enter the maintainer username and password. Support pointed this out so I made sure I was entering the username and password within 14 seconds. Still, no access.
Once I figured out that I was not going to be able to access the firewall by resetting the password, I had to go to plan B. It was time to download a fresh copy for firmware a deploy it via TFTP.
Loading FortiGate firmware image using TFTP :
On a 100D, make sure you plug the Ethernet cable into the MGMT interface as the Internal interface won’t work. This is one more reason why it is very important to backup you configs periodically….
-Colin
2/24/2015
Got burnt by being lazy and running old firmware on a FortiGate 300C. Good new is that the vendor’s support was great.
I have been putting off upgrading one of our Fortinet 300C’s firmware and it came back to bite me yesterday.
While troubleshooting a IPVPN/MPLS issue, I logged into a 300C in one of our data centers and notice the CPU usage was at 100%. I am running 4.0.15 on a FGT 300C which is way behind. I looked at the processes and noticed SQLDB was taking up 85% of the CPU. Not good. Seeing as I have 24×7 support on this box, I called into Fortinet Support to test drive their response. We are looking at migrating our primary data center’s prod firewalls from a pair of Sonicwall E5500’s to a pair of Fortinet 800C’s and I wanted to see how their support for larger firewalls is.
I called the 800 # and spoke with a person within 2 minutes. They then transferred me to an engineer. I had to wait 5 – 7 minutes and then was connected. Once I told him the problem, he sent over a remote support session and took care of the issue within 10 mins. Here are the transcripts from the support session.
It was nice talking to you. Summery of our conversation
– You had issue that CPU usage was 100%. You were running 4.0.15 on FGT 300C
– We did remote session and saw that sqldb process was consuming around 90%
– Checked your logging settings and you were logging in disk
– We disable disk logging by following
config log disk settings
set status disable
end
– Checked system status by following commands and it was back to normal
get system status
get sys performance status
diag system top
– I suggested you to upgrade FGT to at least 5.0.9 and follow release notes I am glad that your
issue has been resolved and as per our discussion I will go ahead and close this ticket.
I was very pleased to see the quick response and resolution from Fortinet on this issue.
-Colin 2/21/15
DHCP options for Mitel 5330 IP Phones
Notes for adding DHCP options to a DHCP scope on a Fortinet firewall. You have to convert the IP’s to hex. Here is the setup for our SMF data center.
Here are the settings from a Windows DHCP server.
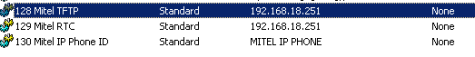
128 Mitel TFTP 172.18.5.173
129 Mitel RTC 172.18.5.173
130 Mitel IP Phone ID
Here are the same settings on a Fortinet 5.2.
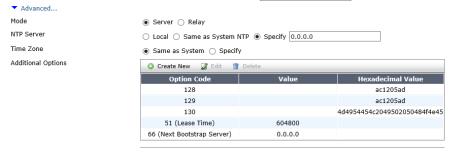
Code: 128 Options: AC1205AD
Code: 129 Options: AC1205AD
Code: 130 Options: 4d4954454c2049502050484f4e45
Enable Interface Mode on FortiWifi 90D’s running FortiOS 5.2
Here is a link to a URL that explains what Switch Mode and Interface Mode are:
http://docs.fortinet.com/d/fortigate-extra-help-switch-mode-vs-interface-mode
If you are like me, you want to keep your firewall configs the same across different Fortinet models. We run 800C’s, 300C/D’s, 100D’s, 90D’s, and 80CM’s and like to keep the rule sets similar. Starting with 5.x, the smaller models (90D’s) are set to Switch Mode. Larger units (100D’s and up) default to interface mode. To enable Interface Mode System -> Dashboard -> Status and enter either of the following commands into the CLI Console:
config system global
show
you will see “set internal-switch-mode switch” is set.
The command to change the FortiGate to Interface mode:
config system global
set internal-switch-mode interface
end
You will most likely get the error “Interface internal is in use. Attribute set operator error, -23, discard the setting Command fail. Return code -23” as the internal Interface you are connected to has a DHCP config bound to it was well as referenced in a ACL. You will need to delete the ACL from System -> Policy and Objects -> IPv4. It’s the outbound rule from the LAN.
You will need to connect to a WAN1 or WAN2 interface so take a look at what that IP is. Disconnect from the Internal Interface and connect to the WAN interface. You will need to assign a static to the network interface on your computer. Now try entering the command again.
Config system global
set internal-switch-mode interface
end
If all goes well, you should be prompted to reboot.
Just in case you want to revert back to Switch Mode, use the syntax below.
Command to change the FortiGate to Switch mode
config system global
set internal-switch-mode switch
end